
Antonio Gabor
Certified Ethical Hacker and Network Security Engineer

Did you ever wonder how is IT different to OT? Is there a veil of mystery covering OT in the cybersecurity space?
Well, if you did, you are in the right place, because we will try to demystify some of the similarities as well as differences in these two overarching domains.
Allow me to share a quick recap about these.
Information Technology (IT) refers to the use of computers, software, networks, and other electronic systems to manage, store, transmit, and retrieve information
IT plays a critical role in modern businesses, organizations, and daily life, facilitating the efficient processing and management of digital data.
Operational Technology (OT) refers to the hardware and software used to monitor, control, and manage physical processes and devices in industrial and operational environments
Unlike IT, which deals with digital information and systems, OT is concerned with real-time control and automation of equipment and processes
OT is commonly found in industries such as manufacturing, energy, transportation, agriculture, and other critical infrastructures.
I will have to reference Marcel Rick-Cen and his Udemy course “Practical Industrial Control System Penetration Testing” as it had the simplest explanation that I could find and that was a very effective one.
IT “moves data”, whereas OT “moves physical systems”!
These are two very different things for sure!
When we are comparing lifecycles that are usually associated with these two, IT has a much shorter operating life of 3-5 years whereas OT ranges from 20-30 years.
The lack of updates for some OT systems is of great concern, contrasting IT systems where we see a continuous cycle of updates throughout their lifetime.
Moreover, there are different security concerns when talking about these two technology domains.
Further, referring to our IT CIA triad, Confidentiality of Information is of utmost importance thus it sits on the top of the pyramid. Now if we imagine a nuclear power plant which lives in the OT domain, produces energy for millions of households, and potential for great catastrophe if say the cooling system is not functioning at the required time, the Availability of operation would most definitely come out as a winner in this one.
You can see this outlined in the diagram below:
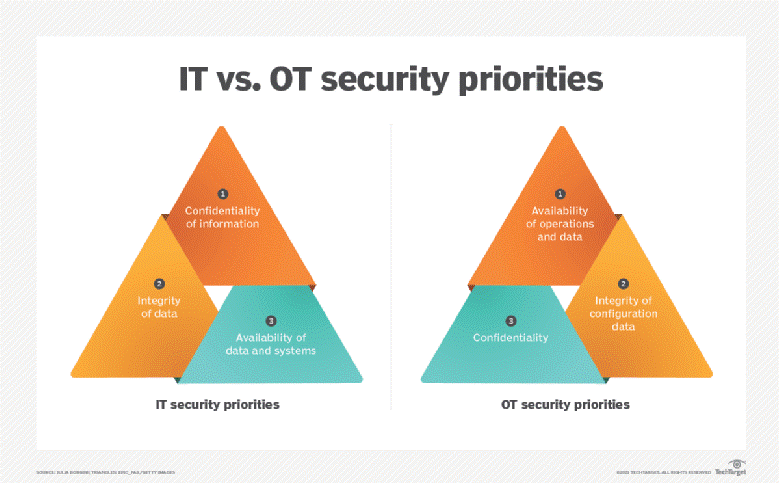
Here are some key differences to be considered when talking about OT vs IT.
- Focus and Scope:
- OT focuses on the control and management of physical processes and devices in real-time industrial environments.
- IT focuses on the digital management of data, systems, and software used to support business operations and information exchange.
- Timing and Responsiveness:
- OT systems require real-time responsiveness to ensure the safe and efficient operation of industrial processes.
- While some IT systems also require real-time processing, many IT tasks can tolerate slightly higher latency and response times.
- Networks and Connectivity:
- OT systems often operate in isolated or air-gapped networks to enhance security and prevent external interference.
- IT systems commonly operate in connected networks to facilitate communication and data exchange.
- Security Concerns:
- OT systems have historically focused more on physical security and safety, but in recent years, the convergence of OT and IT has highlighted the importance of cybersecurity for OT environments.
- IT systems have long dealt with cybersecurity concerns related to data breaches, malware, and unauthorized access.
- Examples of Applications:
- OT applications include manufacturing process control, power grid management, oil and gas production, and water treatment.
- IT applications include software development, data storage and analysis, cloud computing, and communication systems.
- Skillsets and Expertise:
- Professionals working in OT require expertise in industrial automation, process control, and often specialized knowledge about specific industries.
- IT professionals typically specialize in software development, network administration, cybersecurity, database management, and related areas.
In recent years, the distinction between OT and IT has been blurred due to the increasing integration of digital technologies into industrial environments (known as the Industrial Internet of Things or IIoT).
This convergence has led to a greater emphasis on cybersecurity practices within both domains
How do we find OT in the wild?
ICS are a critical part of any OT, and if we discover ICS we have a glimpse into OT.
ICS, or Industrial Control Systems, are specialized computer systems and networks that are used to control and monitor industrial processes and critical infrastructure.
These systems play a crucial role in various industries, including manufacturing, energy, water treatment, transportation, and more. ICS is designed to automate, optimize, and manage complex processes that involve machinery, sensors, actuators, and other physical components.
It is well known that ICS Attack Surface can be easily discovered using OSINT and freely available tools like Shodan or even Google Dorks.
OSINT stands for Open Source Intelligence, which refers to the collection, analysis, and interpretation of information from publicly available sources to gain insights, generate knowledge, and make informed decisions.
Shodan is a specialized search engine that focuses on collecting and indexing information from devices connected to the internet.
Unlike traditional search engines that index websites, Shodan indexes information about various internet-connected devices, including servers, routers, webcams, industrial control systems, IoT (Internet of Things) devices, and more.
Access to Shodan is free, however, there are yearly account sales to look out for as they are of great value to security researchers.
We will first demonstrate a Google Dork, by typing in the search engine:
inurl:/portal/portal.mwsl
This will return over 2000 matches and we can see that some of these Industrial Control Systems are available on Public Internet which should not be the case.
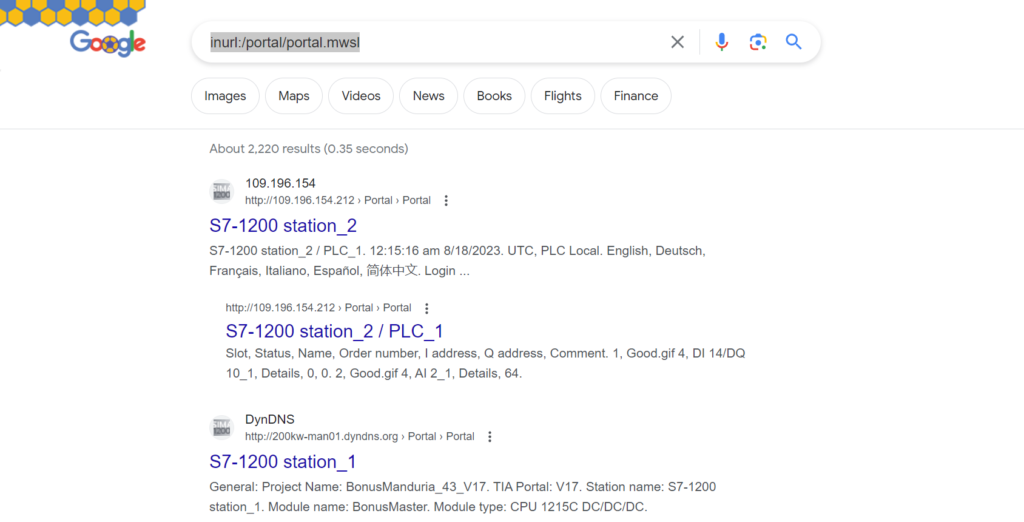
To further explore Public Facing ICS we use Shodan to demonstrate how they can be discovered.
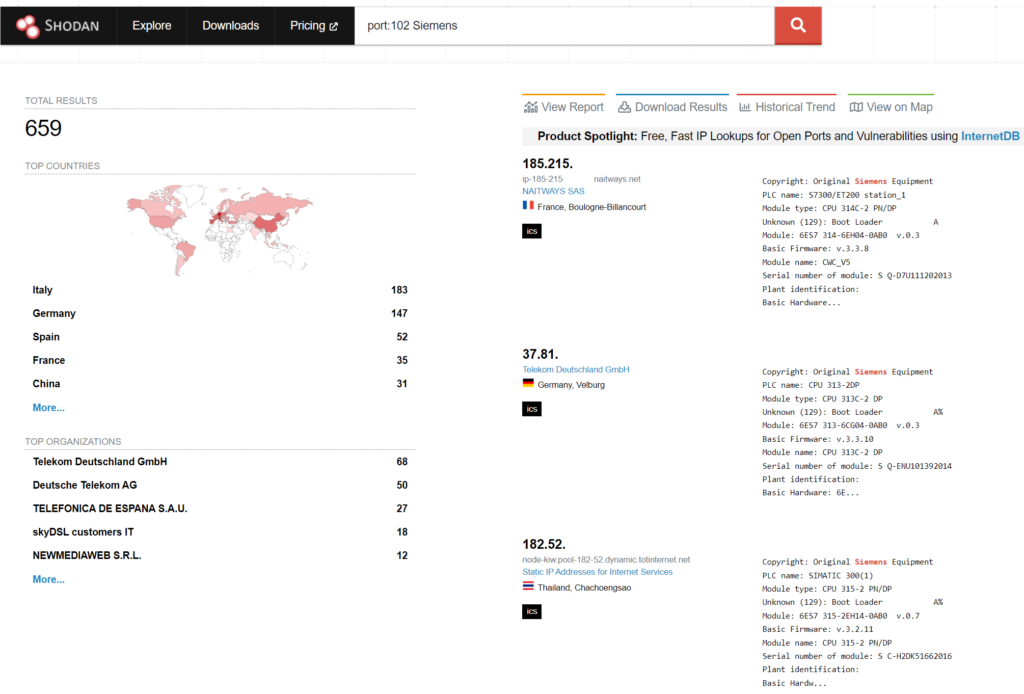
You can observe in the capture above that Shodan not only discovers these systems, but, it further enumerates their models, version and even serial numbers.
To make the matter worse, a list of default credentials can also be easily discovered and there are even repositories on GitHub like SCADAPASS that have them all in one place. If that doesn’t make you think twice regarding security implementation and proper safeguards for ICS nothing will.
Stuxnet worm
To mention one of the greatest OT disruptions that happened till today was the infamous Stuxnet worm.

Source: Wired
Stuxnet specifically targeted industrial control systems (ICS), particularly those used in centrifuge cascades for uranium enrichment. Its primary target was Iran’s nuclear program, specifically the uranium enrichment facilities located in Natanz. The centrifuges were crucial for enriching uranium for nuclear purposes.
Stuxnet aimed to disrupt the operation of these centrifuges by manipulating their rotational speed, causing mechanical stress, and ultimately sabotaging their functionality. This disruption was intended to hinder Iran’s ability to produce enriched uranium for its nuclear program.
The worm’s ability to target and manipulate these industrial control systems marked a significant departure from traditional cyber threats, as it demonstrated the potential for cyber attacks to directly impact physical infrastructure and critical operations.
In January 2010, inspectors with the International Atomic Energy Agency visiting the Natanz uranium enrichment plant in Iran noticed that centrifuges used to enrich uranium gas were failing at an unprecedented rate. The cause was a complete mystery—apparently as much to the Iranian technicians replacing the centrifuges as to the inspectors observing them. Five months later a seemingly unrelated event occurred. A computer security firm in Belarus was called in to troubleshoot a series of computers in Iran that were crashing and rebooting repeatedly. Again, the cause of the problem was a mystery. That is until the researchers found a handful of malicious files on one of the systems and discovered the world's first digital weapon
If you are interested in a full breakdown of malware analysis there are plentiful resources available, however here is one particularly good analysis done by AmrThabet
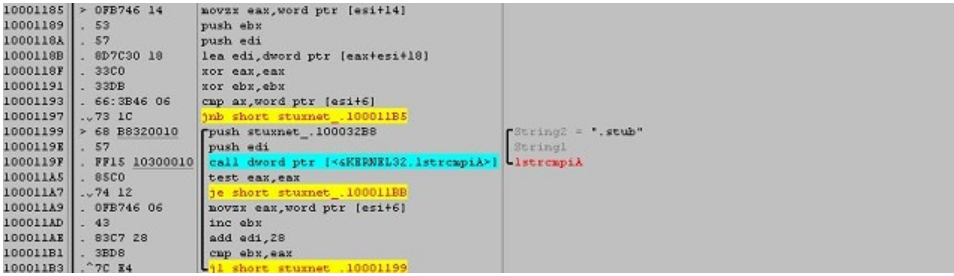
The above code section contains the main Stuxnet DLL file. And this DLL contains all of Stuxnet’s functions, mechanisms, files and rootkits.
(Source: Code project)
How to protect OT environment?
Here are some ways how can we protect our OT environment.
OT cybersecurity aims to ensure the reliability, safety, and integrity of essential processes and equipment.
NIST (National Institute of Standards and Technology) has made the following recommendations:

Here are some additional security measures that you can take to further enhance your OT security:
- Threat Detection and Prevention: Implementing advanced threat detection mechanisms to identify suspicious activities, unauthorized access attempts, and anomalies within industrial networks.
- Vulnerability Management: Regularly assessing and identifying vulnerabilities in OT systems, applications, and devices. Implementing patches and updates to address these vulnerabilities while minimizing operational disruption.
- Network Segmentation: Dividing industrial networks into segments to isolate critical systems from less critical areas and prevent lateral movement of threats.
- Access Control: Implementing strict access controls to limit who can access and modify industrial systems. Employing strong authentication mechanisms to ensure only authorized personnel have access.
- Employee Training: Educating employees and personnel about the importance of cybersecurity practices, social engineering risks, and safe online behaviour.
- Physical Security: Integrating physical security measures with cybersecurity strategies to protect physical access to critical components and equipment.
- Encryption and Data Protection: Implementing encryption to secure data at rest and in transit, ensuring that sensitive information remains confidential and tamper-proof.
OT cybersecurity is a complex and evolving field, as it involves safeguarding systems that can have real-world consequences if compromised.
Organizations must strike a balance between maintaining operational efficiency and embracing the necessary security measures to protect their critical infrastructure and processes from cyber threats.
Further, it is imperative to understand the differences between OT and IT and how they converge together to deliver critical infrastructure services and to be aware of potential dangers that lurk in the dark and how to protect from them.
Stay vigilant and stay safe!
